Ransomware - What is this?
- MZT

- Sep 10, 2022
- 2 min read
Basically it is a program that holds your data or machines ransom until you pay the bad threat actor through the distribution of software.
Who are the most at risk?
Healthcare industry - not much improvement in their technology. Healthcare records are sold on the darkweb for US$200 per record.
eCommerce company - PCI records especially credit card - today per credit card on sale on the darkweb is around US$0.50 per credit card, if it is a fresh card, usually it sells for a higher price before the user knows it was breached and has asked the bank to turn the card off.
The First Instance of Ransomware
1989
The AIDS Trojan* (aka PC Cyborg)
- Created by Dr. Joseph Popp and distributed to 20,000 attendees at the World Health Organization (WHO) AIDS conference - Released on 5¼” floppies - Demanded $189 ransom
The most recent of Ransomware
DarkSide
2021
- Colonial Pipeline attack - Pipeline was shut down for six days - Colonial paid a $4.4 million bitcoin ransom
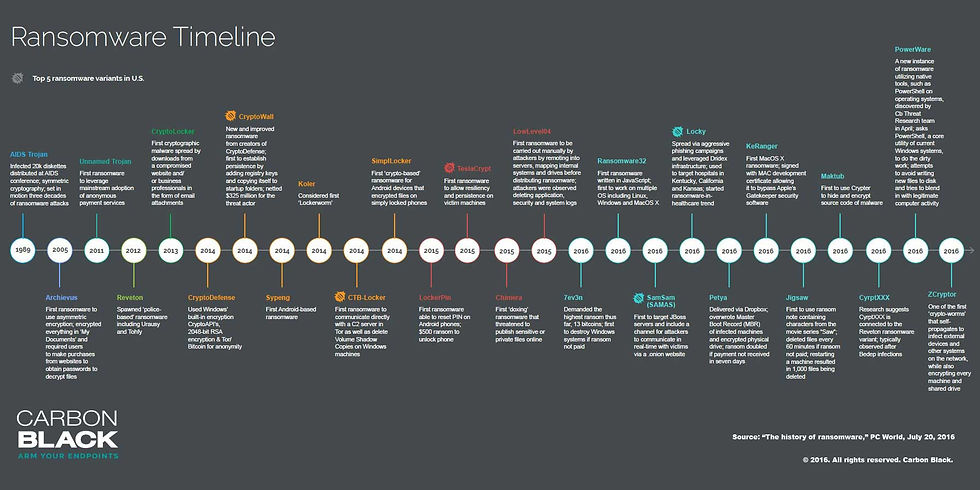
Fig 1
There are various types of Ransomware, the most common channel of infection, is usually via an exposed employee company email system, where the malware would piggy back to the network. There are a variety of tactics, techniques and procedures (TTPs) of ways of access. Therefore it is important to be protected.
Are There Solutions To Solve This?
A good cybersecurity strategy and framework is important for companies, understand their organization's cybersecurity posture allows them to plan and mitigate over weak areas.
For larger organization with a cybersecurity / IT team they are able to plan and execute on their cybersecurity posturing.
For SME/SMB companies, may not have the resources to deploy support and thus usually this function is outsourced to help companies improve their cybersecurity posture. People, Process and Technology (PPT)
Technology - use the right layer of products to help protect the company base on what the company does.
Process - basic process, governance, compliance should be in place to help SME/SMBs cover the basic cyber Essentials.
People - awareness training is very important for the people in the organization, as they are your first line and last line of defence.
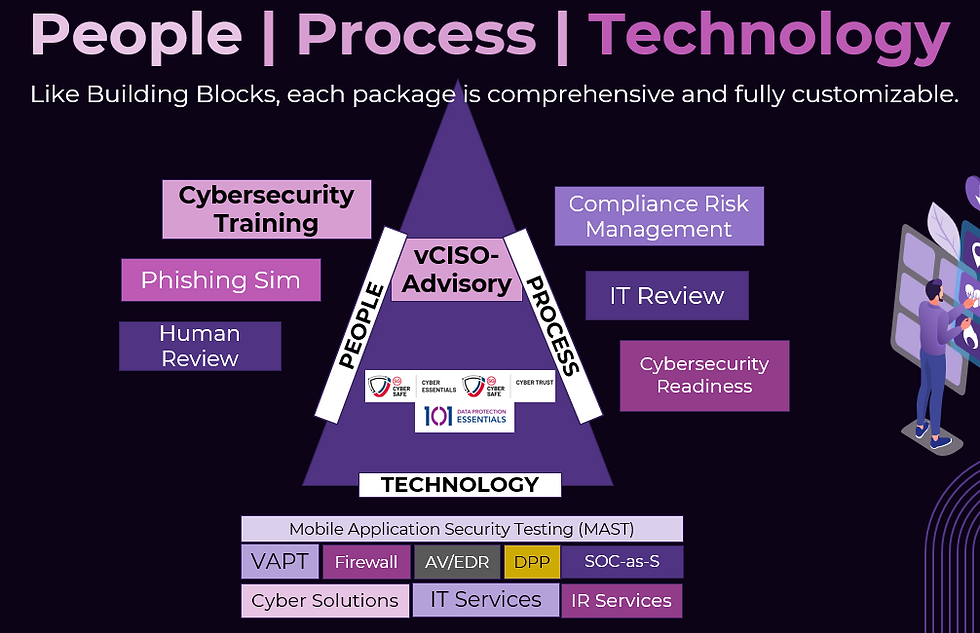
Fig.2
Technical Debt
In software development, technical debt is the implied cost of additional rework caused by choosing an easy solution now; instead of using a better approach
that would take longer.
Look for a cybersecurity company whom can help support your cybersecurity needs. It is always important to get yourself protected and covered today, than after you have been attacked.
Source:
* https://ransomware.org/what-is-ransomware/the-history-of-ransomware/
Fig 1 from Carbon Black Infograph



Comments